Issue Exemption Workflow
Issue Exemptions in STO provide developers and security teams a controlled method to handle security vulnerabilities detected in software delivery pipelines. When a security scan identifies a vulnerability that violates your pipeline's OPA policies, the pipeline will fail to prevent vulnerabilities from reaching production. In cases where immediate remediation isn't feasible or necessary, developers can submit exemption requests for review. Exemptions can be applied at the Project, Organization, or Account level.
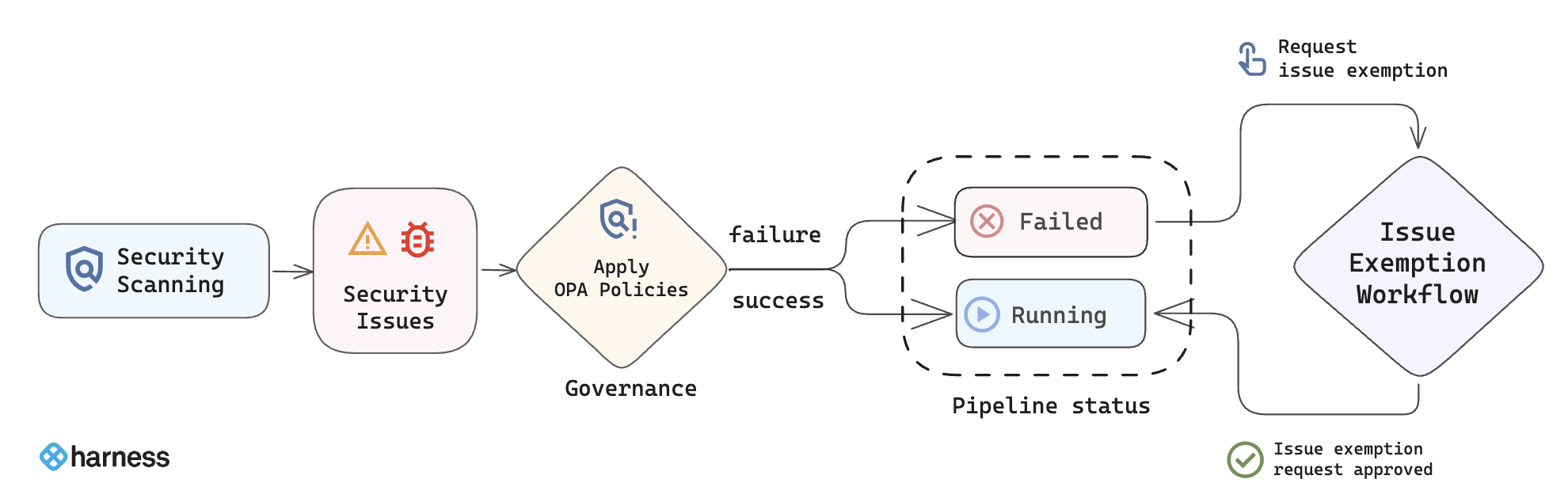
The issue exemption workflow typically includes two stages:
- Requesting an Exemption: Developers initiate exemption requests by providing relevant details, including justification and intended exemption duration. Refer to Request Issue Exemption.
- Managing Exemptions(Approve/Reject): Security teams review exemption requests and choose to approve or reject. Refer to Manage Issue Exemption.
To stay informed about these events, you can set up notifications for exemption requests and status changes.
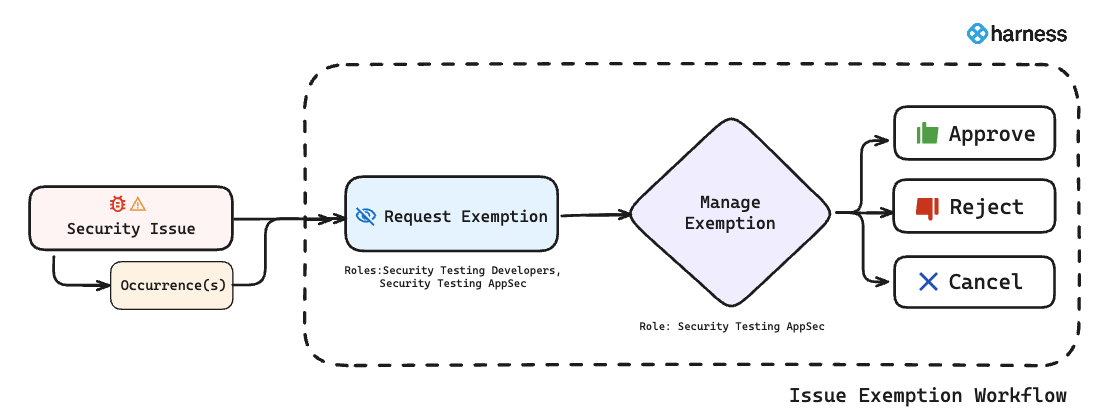
Security Testing Developers and Security Testing AppSec users can request exemptions, but only Security Testing AppSec users can approve them. Refer to Permissions required for issue exemptions for more details.
When exemptions are useful
Here are some reasons wny your organization might want to exempt an issue:
- Your organization is aware of this issue and is actively working on a fix. In the meantime, they want to exempt it from blocking the pipeline.
- The issue is in compliance with your organization's acceptable use policies.
- The security risk is low and remediation would require too much effort or expense.
- The scanner detects an issue but it is, in fact, a false positive.
- You need to exempt an issue so you can deploy a hotfix. In this case, you can request a temporary exemption that expires within your organization's SLA for fixing security issues.
- There are currently no known fixes or remediation steps available for the detected vulnerability. You might want to enable Harness AI to help you remediate your issues using AI.
Required permissions for Issue Exemptions
The table below outlines the permissions required at each scope(Project, Organization, Account) for performing various exemption-related actions. These permissions are part of the Exemptions category in the STO role permissions.
To configure these permissions:
- Navigate to the Project, Organization, or Account settings in Harness.
- Select Roles, then choose or create a role.
- In the Security Tests section, look for the Exemptions category.
- Assign the required permissions:
View,Create/Edit, orApprove/Reject.
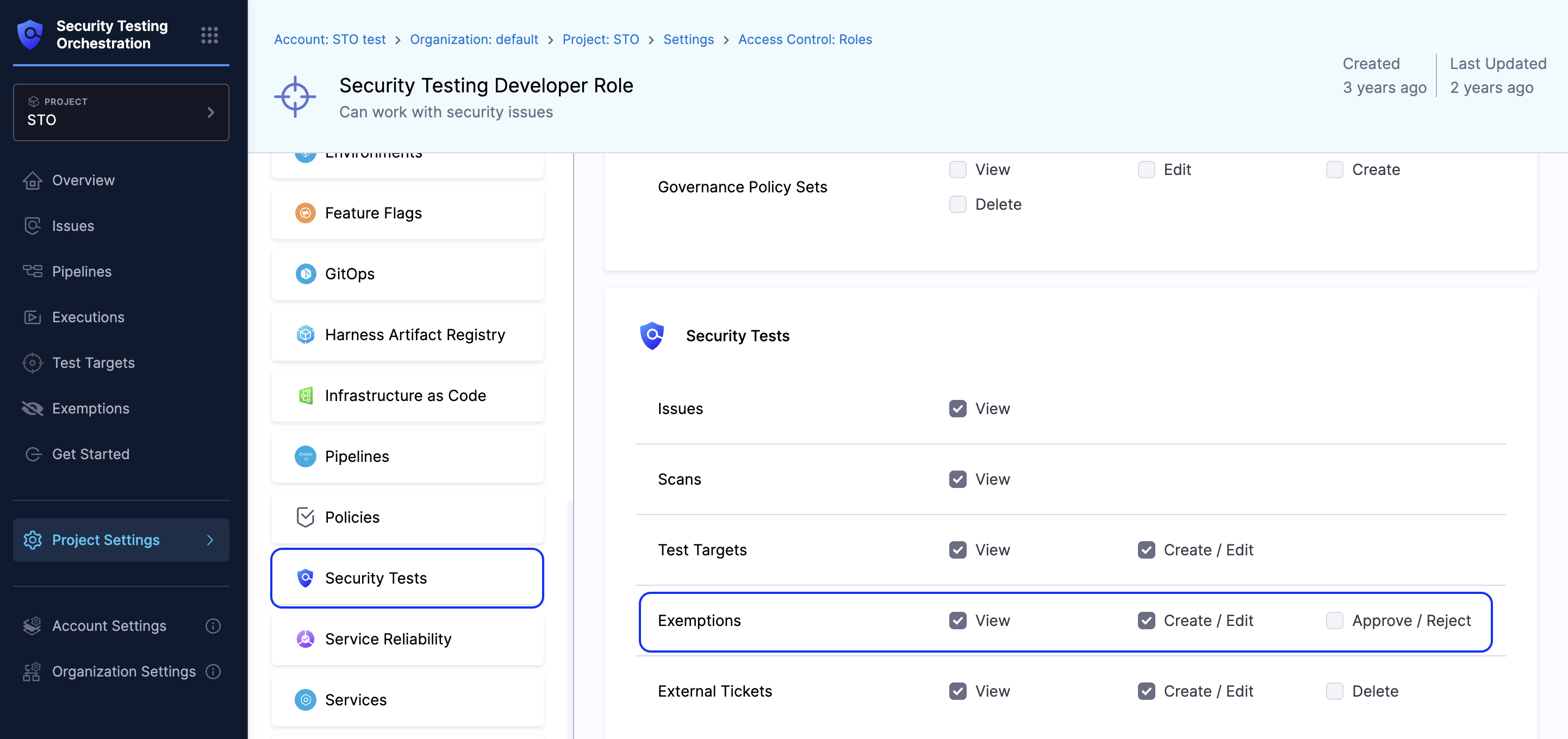
Exemption permissions matrix
| Action | Permission | Project | Org | Account | Notes |
|---|---|---|---|---|---|
| Create an Exemption Request | Create/Edit | ✅ | ❌ | ❌ | Can only be created at the project level. |
| View Exemptions Requests | View | ✅ | ❌ | ❌ | Viewing is based entirely on project-level View permissions. Org/Account level View permissions are not required. |
| Approve or Reject Exemption Requests | View, and 'Approve/Reject' is required, see next row. | ✅ | ❌ | ❌ | Required to access exemption requests. |
| Approve or Reject Exemption Requests | Approve/Reject | ✅ | ✅ | ✅ | Can approve/reject at the requested or higher scope (Org/Account). Exemption applies to all orgs/projects within that scope, even those the reviewer can't access. |
| Re-open an Exemption Request | View, Create/Edit | ✅ | ❌ | ❌ | Reopening is only allowed if the exemption scope is Project, Target, or Pipeline. If approved at Org or Account scope and marked Rejected or Expired, it can’t be reopened—only directly approved again from the status tab. |
Assign Approve/Reject permissions carefully, especially at the Organization or Account level — since actions apply to all underlying scopes, even those the user may not directly manage.
- To view exemption requests across an entire organization or account, the user must have
Viewpermission on each individual project. - Create/Edit is relevant only at the Project level. It is used for creating, cancelling, or reopening exemption requests.
- Approve/Reject permissions are required at the level where the exemption should be applied:
- Project-level: Can approve only for that project.
- Organization-level: Can approve for the entire organization. The exemption applies to all its projects, even those the reviewer doesn't have access to.
- Account-level: Can approve for the entire account. The exemption applies to all its organizations and their projects, even those the reviewer doesn't have access to.
Use "All Resources Including Child Scopes"
Instead of assigning View permission to each project manually, assign the role with a resource group that includes all resources and child scopes. This automatically provides access to all projects and organizations under the account for viewing the exemption requests.
Default Roles and Permissions
Harness provides two RBAC roles specifically for STO users. Here’s how their permissions are set up for Exemptions feature:
- Security Testing Developer: Includes
ViewandCreate/Edit. Use this role for developers who need to raise exemption requests. - Security Testing AppSec: Includes
View,Create/Edit, andApprove/Reject. Use this role for users who review, approve, or reject exemption requests across projects, orgs, or the full account.